4 07 2014
2014 Latest CompTIA Security+ SY0-301 Exam Demo Free Download!
QUESTION 1
An administrator has a network subnet dedicated to a group of users. Due to concerns regarding data and network security, the administrator desires to provide network access for this group only. Which of the following would BEST address this desire?
A. Install a proxy server between the users’ computers and the switch to filter inbound network traffic.
B. Block commonly used ports and forward them to higher and unused port numbers.
C. Configure the switch to allow only traffic from computers based upon their physical address.
D. Install host-based intrusion detection software to monitor incoming DHCP Discover requests.
Answer: C
QUESTION 2
Hotspot Question
Select the appropriate attack from each drop down list to label the corresponding illustrated attack
Instructions: Attacks may only be used once, and will disappear from drop down list if selected. When you have completed the simulation, please select the Done button to submit.
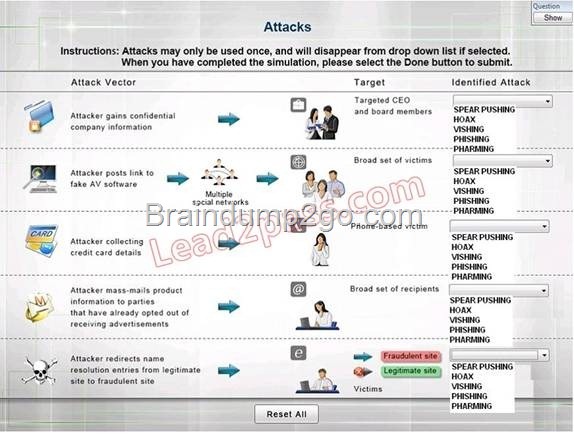
Answer:
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/2014-Latest_7E34/clip_image0024_thumb.jpg)
QUESTION 3
A technician wants to implement a dual factor authentication system that will enable the organization to authorize access to sensitive systems on a need-to-know basis. Which of the following should be implemented during the authorization stage?
A. Biometrics
B. Mandatory access control
C. Single sign-on
D. Role-based access control
Answer: A
QUESTION 4
A security researcher wants to reverse engineer an executable file to determine if it is malicious. The file was found on an underused server and appears to contain a zero-day exploit. Which of the following can the researcher do to determine if the file is malicious in nature?
A. TCP/IP socket design review
B. Executable code review
C. OS Baseline comparison
D. Software architecture review
Answer: C
QUESTION 5
Lab Sim – Configure the Firewall
Task: Configure the firewall (fill out the table) to allow these four rules:
– Only allow the Accounting computer to have HTTPS access to the Administrative server.
– Only allow the HR computer to be able to communicate with the Server 2 System over SCP.
– Allow the IT computer to have access to both the Administrative Server 1 and Administrative Server 2
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/2014-Latest_7E34/clip_image0026_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/2014-Latest_7E34/clip_image0028_thumb.jpg)
Answer:
Use the following answer for this simulation task. Below table has all the answers required for this question.
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/2014-Latest_7E34/clip_image00210_thumb.jpg)
QUESTION 6
Drag and Drop Question
You have been tasked with designing a security plan for your company.
Drag and drop the appropriate security controls on the floor plan.
Instructions:
All objects must be used and all place holders must be filled Order does not matter
When you have completed the simulation, please select the Done button to submit.
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/2014-Latest_7E34/clip_image00212_thumb.jpg)
Answer:
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/2014-Latest_7E34/clip_image00214_thumb.jpg)
QUESTION 7
Matt, the network engineer, has been tasked with separating network traffic between virtual machines on a single hypervisor. Which of the following would he implement to BEST address this requirement? (Select TWO).
A. Virtual switch
B. NAT
C. System partitioning
D. Access-list
E. Disable spanning tree
F. VLAN
Answer: AF
QUESTION 8
Which of the following BEST describes a demilitarized zone?
A. A buffer zone between protected and unprotected networks.
B. A network where all servers exist and are monitored.
C. A sterile, isolated network segment with access lists.
D. A private network that is protected by a firewall and a VLAN.
Answer: A
QUESTION 9
XYZ Corporation is about to purchase another company to expand its operations. The CEO is concerned about information leaking out, especially with the cleaning crew that comes in at night. The CEO would like to ensure no paper files are leaked. Which of the following is the BEST policy to implement?
A. Social media policy
B. Data retention policy
C. CCTV policy
D. Clean desk policy
Answer: D
QUESTION 10
The administrator would like to implement hardware assisted full disk encryption on laptops. Which of the following would MOST likely be used to meet this goal?
A. TPM
B. USB Drive
C. Key Escrow
D. PKI
Answer: A
QUESTION 11
A security administrator wants to check user password complexity. Which of the following is the BEST tool to use?
A. Password history
B. Password logging
C. Password cracker
D. Password hashing
Answer: C
QUESTION 12
Certificates are used for: (Select TWO).
A. Client authentication.
B. WEP encryption.
C. Access control lists.
D. Code signing.
E. Password hashing.
Answer: AD
QUESTION 13
Which of the following is a hardware based encryption device?
A. EFS
B. TrueCrypt
C. TPM
D. SLE
Answer: C
QUESTION 14
Which of the following BEST describes a protective countermeasure for SQL injection?
A. Eliminating cross-site scripting vulnerabilities
B. Installing an IDS to monitor network traffic
C. Validating user input in web applications
D. Placing a firewall between the Internet and database servers
Answer: C
QUESTION 15
Which of the following MOST interferes with network-based detection techniques?
A. Mime-encoding
B. SSL
C. FTP
D. Anonymous email accounts
Answer: B
QUESTION 16
A UNIX administrator would like to use native commands to provide a secure way of connecting to other devices remotely and to securely transfer files. Which of the following protocols could be utilized? (Select TWO).
A. RDP
B. SNMP
C. FTP
D. SCP
E. SSH
Answer: DE
QUESTION 17
Sara, a user, downloads a keygen to install pirated software. After running the keygen, system performance is extremely slow and numerous antivirus alerts are displayed. Which of the following BEST describes this type of malware?
A. Logic bomb
B. Worm
C. Trojan
D. Adware
Answer: C
QUESTION 18
Which of the following would Matt, a security administrator, use to encrypt transmissions from an internal database to an internal server, keeping in mind that the encryption process must add as little latency to the process as possible?
A. ECC
B. RSA
C. SHA
D. 3DES
Answer: D
QUESTION 19
Which of the following describes the process of removing unnecessary accounts and services from an application to reduce risk exposure?
A. Error and exception handling
B. Application hardening
C. Application patch management
D. Cross-site script prevention
Answer: B
QUESTION 20
Which of the following MUST Matt, a security administrator, implement to verify both the integrity and authenticity of a message while requiring a shared secret?
A. RIPEMD
B. MD5
C. SHA
D. HMAC
Answer: D
Passing your CompTIA Security+ SY0-301 Exam by using the latest CompTIA Security+ SY0-301 Exam Demo Full Version: http://www.braindump2go.com/sy0-301.html
2014 Latest Microsoft 70-688 Exam Dump Free Download!(101-110) 2014 Latest CompTIA Network+ N10-005 Exam Demo Free Download!
Comments are currently closed.