3 04 2015
New 70-689 Exam Version Released By Braindump2go Recently For Free Download (211-220)
Are You Interested in Successfully Completing the Microsoft 70-689 Certification Then Start to Earning Salary? Braindump2go has Leading Edge Developed Microsoft Exam Questions that will Ensure You Pass this 70-689 Certification! Braindump2go Delivers you the Most Accurate, Current and Latest Updated 70-689 Certification Exam Questions Availabe with a 100% Money Back Guarantee Promise!
Vendor: Microsoft
Exam Code: 70-689
Exam Name: Microsoft Upgrading Your Skills to MCSA Windows 8.1
QUESTION 211
You administer client computers that run Windows 8 Enterprise deployed by using Windows Deployment Services (WDS).
Your company recently purchased 25 new tablets that run Windows 8 Pro.
For all 25 new tablets, you want to replace the existing Windows 8 Pro installation with Windows 8 Enterprise.
You need to deploy the Windows 8 Enterprise image to all 25 tablets simultaneously by using the existing WDS infrastructure.
What should you do?
A. Start the tablets by using a network boot option.
B. Start the tablets from a default Windows Recovery Environment (WinRE).
C. Start the tablets in Windows Recovery mode.
D. Start the tablets from the Windows To Go workspace.
Answer: A
QUESTION 212
You have 100 client computers that run Windows 8 Pro.
Each computer has a single local hard disk drive, a DVD drive, and an external USB drive.
Each computer has a different set of line-of-business (LOB) desktop applications that are installed locally.
All of the applications store their configurations in the HKEY_Local_Machine\Software registry hive.
You need to design a recovery solution to ensure that you can restore the initial state of the locally installed LOB desktop applications if an application is misconfigured.
The solution must preserve the existing locally stored user data.
What should you do?
A. Enable File History. Restore files by using File History.
B. Create a Microsoft Diagnostics and Recovery Toolset (DaRT) recovery image.
Start the computer from the DaRT image and perform a file restore.
C. Run recimg.exe. Perform a system refresh.
D. Create a system repair disk by using Windows 7 File Recovery.
Start the computer from the Windows 8 Enterprise installation media and perform an
automatic repair,
Answer: C
Explanation:
Reinstalling all of your Desktop apps can be time consuming, so Windows 8 offers a command called recimg.exe to make this easier. recimg creates an image which is used by the refresh facility when restoring Windows. Not only will your personal data and Metro style apps be saved, but so will Desktop apps you have installed at the time you create the image. This can save you a lot of time.
QUESTION 213
At home, you use a desktop computer that runs Windows 8.
At work, you use a laptop that runs Windows 8 and is connected to a corporate network.
You use the same Microsoft account to log on to both computers.
You have a folder with some personal documents on your desktop computer.
The folder must be available and synced between both computers.
You need to ensure that the latest version of these files is available.
What should you do?
A. Move the folder to the Documents folder.
B. Go to PC Settings.
Under Homegroup, select Documents to be Shared.
C. Install SkyDrive for Windows.
In Windows Explorer, move the folder that contains the personal documents to the
SkyDrive folder.
D. Move the folder to the Libraries folder.
E. Go to PC Settings.
Under Sync your settings, enable App settings.
F. Right-click the folder and click Properties.
Under Security, provide Full Control for the Microsoft account.
Answer: C
QUESTION 214
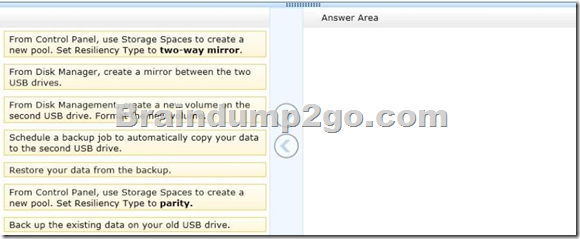
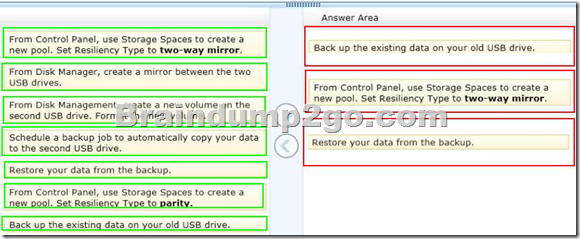
Drag and Drop Questions
You have a computer that runs Windows 8.
You have a 1-terabyte external hard drive.
You purchase a second 1-terabyte external hard drive.
You need to create a fault-tolerant volume that includes both external hard drives.
You also need to ensure that additional external hard drives can be added to the volume.
Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
Answer:
Explanation:
To create a storage space, you’ll have to connect two or more additional drives to your computer you can’t use your system drive for this. The drives can be either internal or external drives.
You can open the Storage Spaces configuration window from the Control Panel or by bringing up the Start screen with the Windows key, typing "Storage Spaces," clicking the Settings category and selecting the Storage Spaces shortcut.
Select the drives you want to use for the storage space and click the "Create pool" button to continue. You’ll lose any files that are already on the drive – copy any important files off the drives before pooling them.
You can add additional drives later.
The resiliency type controls how Windows handles your data.
There are four options:
– None: Windows will store only a single copy of your .
You’ll lose the data if one of your drives fails, but no space will be used on backups.
– Two-way mirror: Windows will store two copies of your data.
If one of your drives fails, you won’t lose your data.
This requires at least two drives.
– Three-way mirror: Windows will store three copies of your data.
If one or two of your drives fails, you won’t lose your data.
This requires at least three drives.
– Parity: Windows stores parity information with the data, protecting you from a single drive failure. Parity uses drive space more efficiently than mirroring, but file access times are slower. Parity is ideal for drives with large, infrequently updated files, such as video files. Reference: How to Use Windows 8s Storage Spaces to Mirror & Combine Drives
QUESTION 215
You administer computers that run Windows 8 Pro and are members of an Active Directory domain.
The computers are encrypted with BitLocker and are configured to store BitLocker encryption passwords in Active Directory.
A user reports that he has forgotten the BitLocker encryption password for volume E on his computer.
You need to provide the user a BitLocker recovery key to unlock the protected volume.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Ask the user for his computer name.
B. Ask the user to run the manage-bde -unlock E: -pw command.
C. Ask the user for his logon name.
D. Ask the user for a recovery key ID for the protected volume.
Answer: AD
QUESTION 216
You administer laptops that run Windows 8 Enterprise and are members of an Active Directory domain.
Users travel frequently and access domain resources from inside client networks or from their home network.
You want to manage the laptops when they are connected to the company network from the external networks.
You need to ensure that the laptops can be managed and maintained while users are not logged on to the computers.
Which of the following should you recommend?
A. Remote Assistance
B. Windows Remote Management (WinRM)
C. DirectAccess
D. Remote Desktop
Answer: C
Explanation:
DirectAccess, introduced in the Windows 7 and Windows Server 2008 R2 operating systems, allows remote users to securely access enterprise shares, web sites, and applications without connecting to a virtual private network (VPN). DirectAccess establishes bi-directional connectivity with a user’s enterprise network every time a users DirectAccess-enabled portable computer connects to the Internet, even before the user logs on. Users never have to think about connecting to the enterprise network and IT administrators can manage remote computers outside the office, even when the computers are not connected to the VPN. Forefront Unified Access Gateway (UAG) 2010 extends the benefits of DirectAccess across your infrastructure, enhancing scalability and simplifying deployment and ongoing management.
http://technet.microsoft.com/en-us/network/dd420463.aspx
QUESTION 217
You support computers that run Windows 8 Pro and are members of an Active Directory domain. Several desktop computers are located in a subnet that is protected by a firewall.
The firewall allows incoming TCP connections only to ports 80 and 443.
You want to manage disk volumes on the desktop computers from your computer, which is located outside the protected subnet.
You need to configure the network to support the required remote administration access.
What should you do?
A. Enable Remote Desktop on the desktop computers.
B. Run the winrm quickconfig command on your computer.
C. Install Remote Server Administration Tools (RSAT) on your computer.
D. Run the winrm quickconfig command on the desktop computers.
Answer: D
QUESTION 218
You support desktop computers and tablets that run Windows 8 Enterprise.
All of the computers are able to connect to your company network from the Internet by using DirectAccess.
Your company wants to deploy a new application to the tablets.
The deployment solution must meet the following requirements:
– The application is not accessible if a user is working offline.
– The application is stored on an internal solid-state drive (SSD) on the tablets.
– The application is isolated from other applications.
– The application uses the least amount of disk space.
You need to deploy the new application to the tablets.
What should you do?
A. Deploy the application as an Application Virtualization (App-V) package.
Install the App-V 4.6 client on the tablets.
B. Deploy the application as a published application on the Remote Desktop server.
Create a Remote Desktop connection on the tablets.
C. Install the application on a local drive on the tablets.
D. Install the application in a Windows To Go workspace.
E. Install Hyper-V on tablets. Install the application on a virtual machine.
F. Publish the application to Windows Store.
G. Install the application within a separate Windows 8 installation in a virtual hard disk (VHD) file.
Configure the tablets with dual boot.
H. Install the application within a separate Windows 8 installation in a VHDX file.
Configure tablets with dual boot.
Answer: A
Explanation:
Microsoft Application Virtualization (App-V) enables enterprises to meet the needs of users and IT by empowering anywhere productivity and accelerated application deployment. App-V provides anywhere user access to applications that available on any authorized device without application installs. Virtual applications and user settings are preserved whether users are online or offline. App-V increases business agility through faster application deployment and updates with no user interruptions. It minimizes conflicts between applications, allowing enterprises to reduce application compatibility testing time. App-V together with Microsoft User State Virtualization (USV) provides users witha consistent experience and reliable access to applications and business data, no matter their location and connection to the Internet.
http://www.microsoft.com/en-us/windows/enterprise/products-and-technologies/virtualization/app-v.aspx
QUESTION 219
You support desktop computers and tablets that run Windows 8 Enterprise.
All of the computers are able to connect to your company network from the Internet by using DirectAccess.
Your company wants to deploy a new application to the tablets.
The deployment solution must meet the following requirements:
– Users have offline access to the application only within the first seven days following their latest online session.
– The application uses the least amount of disk space.
You need to deploy the new application to the tablets.
What should you do?
A. Deploy the application as an Application Virtualization (App-V) package.
Install the App-V client on the tablets.
B. Deploy the application as a published application on the Remote Desktop server.
Create a Remote Desktop connection on the tablets.
C. Install the application on a local drive on the tablets.
D. Install the application in a Windows To Go workspace.
E. Install Hyper-V on tablets. Install the application on a virtual machine.
F. Publish the application to Windows Store.
G. Install the application within a separate Windows 8 installation in a virtual hard disk (VHD) file.
Configure the tablets with dual boot.
H. Install the application within a separate Windows 8 installation in a VHDX file.
Configure tablets with dual boot.
Answer: A
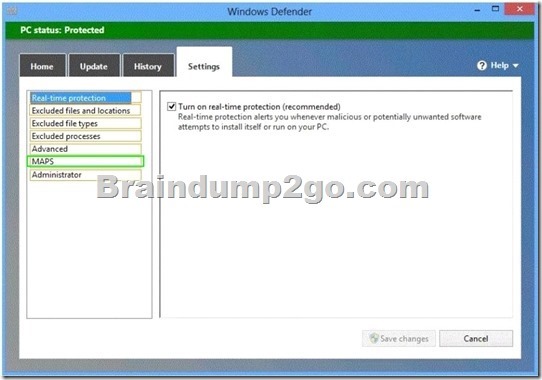
QUESTION 220
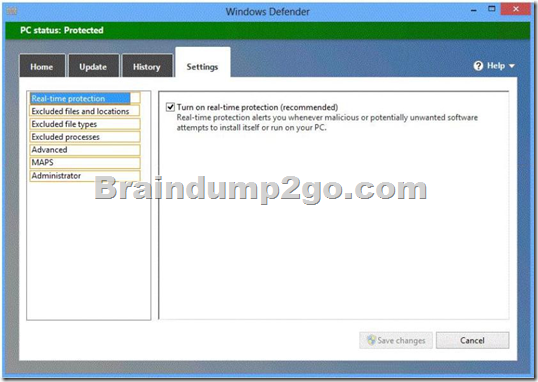
Hotspot Questions
You have computers that run Windows 8 Pro and are configured as a workgroup.
Each computer is scheduled to run a Windows Defender full scan every morning at 07:00.
Users report that they are unable to view previous instances of detected malware when they arrive to work.
You need to ensure that all users can see previous instances of detected malware in Windows Defender.
Which option on the Settings tab should you select? (To answer, select the appropriate option in the answer area.)
Answer:
For those who feel the overwhelming anxiety before their 70-689 exam,Braindump2go Latest updated 70-689 Exam Dumps will help you Pass 100% in a short time preparation! 70-689 Exam Dumps PDF & VCE Full Version Instant Download!
http://www.braindump2go.com/70-689.html
Microsoft 70-689 Free Braindumps – Pass 70-689 Exam With Braindump2go Free Microsoft 70-689 Q&As (201-210) Microsoft 70-689 Practice Questions Free Download From Braindump2go (221-230)
Comments are currently closed.