16 02 2017
[2017-New-Dumps]Cisco 600-199 VCE and 600-199 PDF Dumps Free Download in Braindump2go[Q1-Q10]
2017 Feb. New Cisco 600-199 Exam Questions and Answers Updated Today!
Free Download 600-199 Dumps and 600-199 VCE 60Q&As from www.braindump2go.com Today!
100% Real Exam Questions! 100% Exam Pass Guaranteed!
1.|NEW 600-199 Dumps and 600-199 PDF 60Q&As Download:
http://www.braindump2go.com/600-199.html
2.|NEW 600-199 Exam Questions and 600-199 VCE Download:
https://1drv.ms/f/s!AvI7wzKf6QBjgkm_DtWXO9h1Xwmc
QUESTION 1
Which describes the best method for preserving the chain of evidence?
A. Shut down the machine that is infected, remove the hard drive, and contact the local authorities.
B. Back up the hard drive, use antivirus software to clean the infected machine, and contact the local
authorities.
C. Identify the infected machine, disconnect from the network, and contact the local authorities.
D. Allow user(s) to perform any business-critical tasks while waiting for local authorities.
Answer: C
QUESTION 2
Which will be provided as output when issuing the show processes cpu command on a Cisco IOS router?
A. router configuration
B. CPU utilization of device
C. memory used by device processes
D. interface processing statistics
Answer: B
QUESTION 3
Refer to the exhibit. Which protocol is used in this network traffic flow?
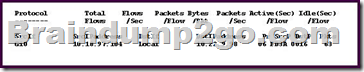
A. SNMP
B. SSH
C. DNS
D. Telnet
Answer: B
QUESTION 4
Which two types of data are relevant to investigating network security issues? (Choose two.)
A. NetFlow
B. device model numbers
C. syslog
D. routing tables
E. private IP addresses
Answer: AC
QUESTION 5
In the context of a network security device like an IPS, which event would qualify as having the highest severity?
A. remote code execution attempt
B. brute force login attempt
C. denial of service attack
D. instant messenger activity
Answer: A
QUESTION 6
Which event is likely to be a false positive?
A. Internet Relay Chat signature with an alert context buffer containing #IPS_ROCS Yay
B. a signature addressing an ActiveX vulnerability alert on a Microsoft developer network documentation page
C. an alert for a long HTTP request with an alert context buffer containing a large HTTP GET request
D. BitTorrent activity detected on ephemeral ports
Answer: B
QUESTION 7
Given a Linux machine running only an SSH server, which chain of alarms would be most concerning?
A. brute force login attempt from outside of the network, followed by an internal network scan
B. root login attempt followed by brute force login attempt
C. Microsoft RPC attack against the server
D. multiple rapid login attempts
Answer: A
QUESTION 8
If a company has a strict policy to limit potential confidential information leakage, which three alerts would be of concern? (Choose three.)
A. P2P activity detected
B. Skype activity detected
C. YouTube viewing activity detected
D. Pastebin activity detected
E. Hulu activity detected
Answer: ABD
QUESTION 9
Which event is actionable?
A. SSH login failed
B. Telnet login failed
C. traffic flow started
D. reverse shell detected
Answer: D
QUESTION 10
Which would be classified as a remote code execution attempt?
A. OLE stack overflow detected
B. null login attempt
C. BitTorrent activity detected
D. IE ActiveX DoS
Answer: A
!!!RECOMMEND!!!
1.|NEW 600-199 Dumps and 600-199 PDF 60Q&As Download:
http://www.braindump2go.com/600-199.html
2.|NEW 600-199 Study Guide:
https://youtu.be/AgHGXrA9L1M
[2017-New]Braindump2go Cisco 400-251 Exam VCE and PDF 1106Q&As for 100% Passing 400-251 Exam[Q116-Q130] [2017-New-Dumps]Cisco 600-199 Dump-VCE and PDF(Full Version)60q Download in Braindump2go[Q11-Q20]
Comments are currently closed.