3 03 2023
[March-2023]Braindump2go 300-430 PDF and 300-430 VCE 300-430 135Q Free Offered[Q69-Q110]
March/2023 Latest Braindump2go 300-430 Exam Dumps with PDF and VCE Free Updated Today! Following are some new Braindump2go 300-430 Real Exam Questions!
QUESTION 69
Which three characteristics of a rogue AP pose a high security risk? (Choose three.)
A. open authentication
B. high RSSI
C. foreign SSID
D. accepts clients
E. low RSSI
F. distant location
Answer: ACD
Explanation:
https://www.cisco.com/c/en/us/td/docs/wireless/controller/74/configuration/guides/consolida ted/b_cg74_CONSOLIDATED/b_cg74_CONSOLIDATED_chapter_010111001.html
QUESTION 70
An administrator receives reports of many interferers in the wireless network and wants to get the location of these interferers from the maps in Cisco Prime Infrastructure.
When looking at the floor plans/maps, the administrator does not see any interferers, but can see all wireless clients located successfully.
Which two statements define the cause of the issue? (Choose two.)
A. MSE is not added to Cisco Prime infrastructure and synchronized.
B. Interferer tracking is not enabled on the MSE.
C. SNMP between Cisco Prime Infrastructure and the WLC is failing.
D. Context Aware Service tracking limit has already been reached with tracking other elements.
E. NSMP communication is inactive with the WLC.
Answer: AB
Explanation:
https://www.cisco.com/c/en/us/support/docs/wireless/5500-series-wireless-controllers/112139- cleanair-uwn-guide-00.html
QUESTION 71
You plan to implement Cisco Identity Based Networking Services on a Cisco Catalyst 3850 Series Switch. Which switch command is required when configuring downloadable ACLs?
A. authentication display new-style
B. ip device tracking
C. dot1x system-auth-control
D. aaa session-id common
Answer: B
Explanation:
https://www.cisco.com/en/US/docs/ios-xml/ios/sec_usr_8021x/configuration/15-2mt/sec-ieee- 802x-acl-assign.html
QUESTION 72
Which CLI command do you use to shut down the 2.4 GHz radio of the Floor1_AP1 AP on a Cisco 3850 Switch?
A. ap name Floor1_AP1 dot11 shutdown 24ghz
B. ap name Floor1_AP1 dot11 5ghz shutdown
C. ap name Floor1_AP1 dot11 24ghz shutdown
D. ap name Floor1_AP1 shutdown dot11 24ghz
Answer: C
QUESTION 73
Which three properties are used for client profiling of wireless clients? (Choose three.)
A. HTTP user agent
B. DHCP
C. MAC OUI
D. hostname
E. OS version
F. IP address
Answer: ABC
Explanation:
The user can configure these policies and enforce end-points with specified policies. The wireless clients will be profiled based on MAC OUI, DHCP, HTTP user agent (valid Internet is required for successful HTTP profiling). The WLC uses these attributes and predefined classification profiles to identify devices.
https://www.cisco.com/c/en/us/td/docs/wireless/controller/technotes/7-5/NativeProfiling75.html
QUESTION 74
Which command set configures a Cisco Catalyst 9800 Series Wireless Controller so that the client traffic enters the network at the AP switch port?

A. Option A
B. Option B
C. Option C
D. Option D
Answer: D
Explanation:
There is no “wireless flexconnect” command. Use the “wireless profile Policy” command.
https://www.cisco.com/c/en/us/td/docs/wireless/controller/9800/17-1/cmd-ref/b_wl_17_1_cr/configuration-commands-g-to-z.html#wp5169136690
There is no “Local switching” command. Use the “no central switching” command.
https://www.cisco.com/c/en/us/td/docs/wireless/controller/9800/17-1/cmd-ref/b_wl_17_1_cr/configuration-commands-a-to-f.html#wp3034709985
QUESTION 75
An engineer completed the basic installation for two Cisco CMX servers and is in the process of configuring high availability, but it fails.
Which two statements about the root of the issue are true? (Choose two.)
A. The Cisco CMX instances are installed in the same subnet.
B. The types of the primary and secondary Cisco CMX installations differ.
C. The delay between the primary and secondary instance is 200 ms.
D. The sizes of the primary and secondary Cisco CMX installations differ.
E. Both Cisco CMX installations are virtual.
Answer: BD
Explanation:
Pre-requisites for HA
Both the primary and the secondary server should be of the same size and the same type (VM or physical appliance).
Both the primary and the secondary server should have the same Cisco CMX version.
Both the primary and the secondary server should be connected on the same subnet.
Both the primary and the secondary server should be connected on the same subnet if Layer 2 HA is required.
Both the primary and the secondary server should be IP connected with delay of less then 250ms if Layer 3 HA is used.
From Cisco CMX release 10.6.2, NTP server settings must be configured on both Primary and Secondary server instance before HA pairing starts. We recommend that you use the same NTP server on both Primary and Secondary. As a Cisco CMX admin you can also use a dedicated NTP for Primary and Secondary.
https://www.cisco.com/c/en/us/td/docs/wireless/mse/10-6/cmx_config/b_cg_cmx106/managing_cisco_cmx_system_settings.html
QUESTION 76
An engineer wants the wireless voice traffic class of service to be used to determine the queue order for packets received, and then have the differentiated services code point set to match when it is resent to another port on the switch.
Which configuration is required in the network?
A. Platinum QoS configured on the WLAN
B. WMM set to required on the WLAN
C. msl qos trust dscp configured on the controller switch port
D. msl qos trust cos configured on the controller switch port
Answer: D
Explanation:
When you enter the mls qos trust cos command on a port, the switch uses the CoS marking on incoming packets in order to put the packet in the right queue. When the packet is resent, the switch makes the DSCP value correspond to the CoS.
https://www.cisco.com/c/en/us/support/docs/wireless-mobility/voice-over-wireless-lan-vowlan/116056-technote-qos-00.html#anc3
QUESTION 77
Refer to the exhibit. You enter the command on a Cisco Catalyst 3850 Series Switch that runs Cisco ISO XE. What does the command do?
A. It defines the user identity or the device identity to be validated by the RADIUS server.
B. It captures information on the length of the authorized session, as well as the bandwidth usage of the client.
C. It defines the RADIUS server used to track which sessions are still active.
D. It defines the level of access of the user or the device.
Answer: D
QUESTION 78
A wireless engineer has performed a Wireshark capture on an 802.1x authentication process to troubleshoot a connectivity issue.
Which two types of packet does the EAP contain? (Choose two.)
A. EAP complete
B. EAP response
C. EAP failure
D. EAP request
E. EAP reply
Answer: BD
QUESTION 79
Which EAP method can an AP use to authenticate to the wired network?
A. EAP-GTC
B. EAP-MD5
C. EAP-TLS
D. EAP-FAST
Answer: D
Explanation:
Enables or disables Extensible Authentication Protocol-Flexible Authentication via Secure Tunneling (EAP-FAST) authentication.
https://www.cisco.com/c/en/us/td/docs/wireless/controller/8-0/cmd- ref/b_cr80/config_commands_a_to_i.html
QUESTION 80
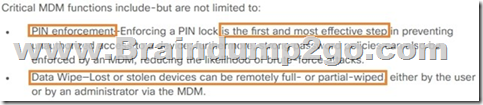
An engineer is considering an MDM integration with Cisco ISE to assist with security for lost devices.
Which two functions of MDM increase security for lost devices that access data from the network? (Choose two.)
A. PIN enforcement
B. Jailbreak/root detection
C. data wipe
D. data encryption
E. data loss prevention
Answer: AC
Explanation:
QUESTION 81
An engineer is setting up a new unique NAD on a Cisco ISE.
Which two parameters must be configured? (Choose two.)
A. device hostname
B. device password
C. RADIUS fallback
D. device IP address
E. RADIUS shared secret
Answer: AD
QUESTION 82
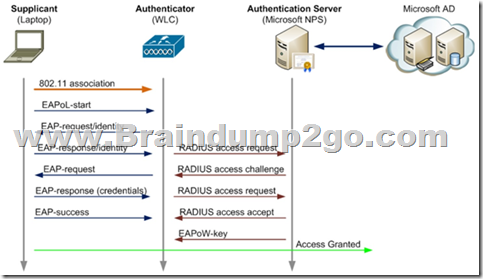
An engineer has configured the wireless controller to authenticate clients on the employee SSID against Microsoft Active Directory using PEAP authentication.
Which protocol does the controller use to communicate with the authentication server?
A. EAP
B. 802.1X
C. RADIUS
D. WPA2
Answer: C
Explanation:
EAP is exchanged between supplicant and authenticator and RADIUS Is used between authenticator and Auth server.
QUESTION 83
Which condition introduce security risk to a BYOD policy?
A. enterprise-managed MDM platform used for personal devices
B. access to LAN without implementing MDM solution
C. enforcement of BYOD access to internet only network
D. enterprise life-cycle enforcement of personal device refresh
Answer: B
QUESTION 84
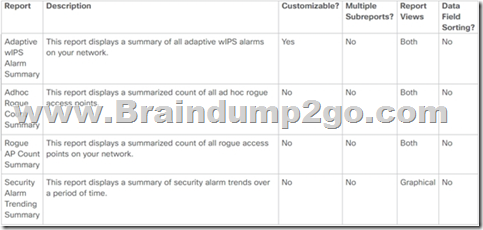
Drag and Drop Question
A wireless engineer wants to schedule monthly security reports in Cisco Prime infrastructure.
Drag and drop the report the from the left onto the expected results when the report is generated on the right.
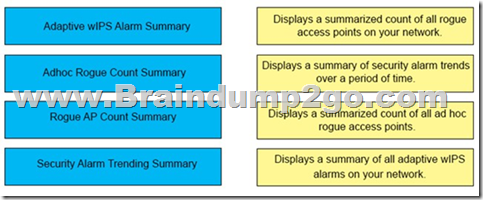
Answer:
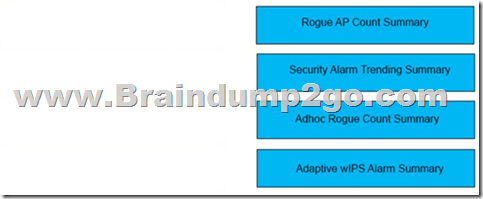
Explanation:
QUESTION 85
When configuring a Cisco WLC, which CLI command adds a VLAN with VLAN ID of 30 to a FlexConnect group named BranchA-FCG?
A. config flexconnect BranchA-FCG vlan 30 add
B. config flexconnect group BranchA-FCG vlan add 30
C. config flexconnect group BranchA-FCG vlan 30 add
D. config flexconnect BranchA-FCG vlan add 30
Answer: B
Explanation:
https://www.cisco.com/c/en/us/td/docs/wireless/controller/8-5/config-guide/b_cg85/flexconnect_groups.html
QUESTION 86
An engineer must implement intrusion protection on the WLAN. The AP coverage is adequate and on-channel attacks are the primary concern. The building is historic, which makes adding APs difficult. Which Ap mode and submode must be implemented?
A. Ap mode: local, Ap submode: WIPS
B. Ap mode: monitor, Ap submode: WIPS
C. Ap mode: monitor, Ap submode: none
D. Ap mode: local, Ap submode: none
Answer: A
QUESTION 87
Refer to the exhibit. An engineer deployed a Cisco WLC using local EAP. Users who are configured for EAP-PEAP cannot connect to the network. Based on the local EAP debug controller provided, why is the client unable to connect?
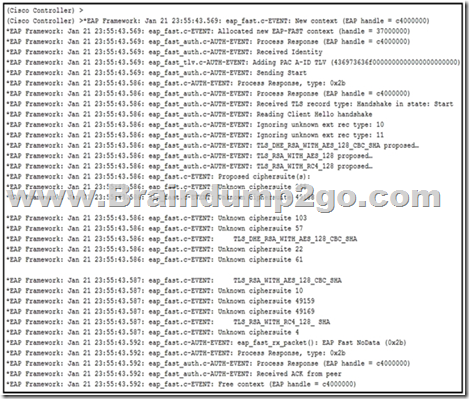
A. The client is falling to accept certificate.
B. The Cisco WLC is configured for the incorrect date.
C. The user is using invalid credentials.
D. The Cisco WLC local EAP profile is misconfigured.
Answer: D
Explanation:
User is configured for PEAP authentication. WLC starts EAP-FAST context (Line 3). -> EAP Profile on the WLC needs to be corrected to use PEAP.
QUESTION 88
Which two configurations are applied on the WLC to enable multicast, check multicast stream subscriptions, and stream content only to subscribed clients? (Choose two)
A. Enable IGMP snooping
B. Set the IGMP timeout to 180 seconds
C. Enable broadcast forwarding
D. Enable 802.3x flow control mode.
E. Set the AP multicast to 238.255.255.255
Answer: AC
Explanation:
https://www.cisco.com/c/en/us/support/docs/wireless-mobility/wireless-lan-wlan/81671-multicast-wlc-lap.html
QUESTION 89
Which configured is applied to prevent the network from a Layer 2 flooding of multicast frames with a seamless transfer of multicast data to the client when roaming from one controller to another?
A. Enable IGMPv3 on the central Layer 3 switch.
B. Enable IGMP snooping on the WLC
C. Create multicast groups on the central Layer 3 switch.
Answer: B
Explanation:
https://www.cisco.com/c/en/us/support/docs/wireless-mobility/wireless-lan-wlan/81671-multicast-wlc-lap.html
QUESTION 90
A corporation has a wireless network where all access points are configured in FlexConnect. The WLC has a Data WLAN and a VoWiFi WLAN implemented where centrally-switched is configured for the APs. Which QoS configuration must be implemented for the wireless packets to maintain the marking across the wired and wireless network?
A. Enable CAC
B. Trust DSCP
C. Set QoS to Platinum
D. Allow WMM
Answer: B
QUESTION 91
What is configured to use more than one port on the OEAP to extend the wired network’s?
A. AAA override
B. client load balancing
C. remote LAN ACL
D. remote LAN
Answer: D
QUESTION 92
An engineer must create an account to log in to the CLI of an access point for troubleshooting. Which configuration on the WLC will accomplish this?
A. ReadWrite User Access Mode
B. Global Configuration Enable Password
C. SNMP V3 User
D. Allow New Telnet Sessions
Answer: B
QUESTION 93
A corporation is spread across different countries and uses MPLS to connect the offices. The senior management wants to utilize the wireless network for all the employees. To ensure strong connectivity and minimize delays, an engineer needs to control the amount of traffic that is traversing between the APs and the central WLC.
Which configuration should be used to accomplish this goal?
A. FlexConnect mode with OfficeExtend enabled
B. FlexConnect mode with local authentication
C. FlexConned mode with central switching enabled
D. FlexConnect mode with central authentication
Answer: B
Explanation:
https://www.cisco.com/c/en/us/td/docs/wireless/controller/72/configuration/guide/cg/cg_flex connect.html#wp1241304

QUESTION 94
An engineer must track guest traffic flow using the WLAN infrastructure. Which Cisco CMX feature must be configured and used to accomplish this tracking?
A. analytics
B. connect and engage
C. presence
D. detect and locate.
Answer: C
Explanation:
The Cisco CMX Presence Analytics service is a comprehensive analytics and engagement platform that uses APs to detect visitor presence based on their mobile devices’ Received Signal Strength Indication (RSSI). The AP detects these client mobile devices irrespective of the latter’s wireless association state as long as they are within the specified signal range, and the wireless option is enabled on the mobile device (ability to detect devices wirelessly even if they are not connected to the network
https://www.cisco.com/c/en/us/td/docs/wireless/mse/10-4/cmx_config/b_cg_cmx104/the_cisco_cmx_presence_analytics_service.html
QUESTION 95
Refer to the exhibit. An engineer tries to manage the rogues on the Cisco WLC. Based on the configuration, which AP is marked as malicious by the controller?
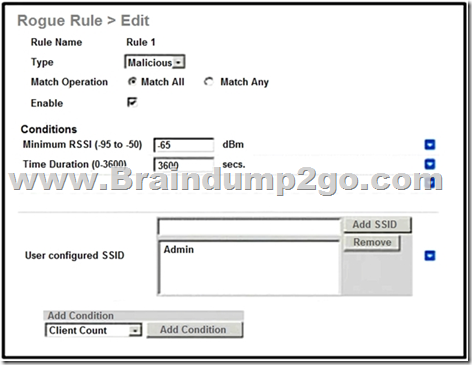
A. rogue AP with SSlD admin seen for 4000 seconds and heard at -60 dBm
B. rogue AP with SSID admin seen for 3000 seconds and heard at -70 dBm
C. rogue AP with SSlD admin seen for 4000 seconds and heard at -70 dBm
D. rogue AP with SSID admin seen for 3000 seconds and heard at -60 dBm
Answer: A
Explanation:

QUESTION 96
An engineer must achieve the highest level of location accuracy possible for a new mobile application. Which technology must be implemented for this use case?
A. Time Difference of Arrival
B. Bluetooth Low Energy
C. RSS lateration
D. ToA lateration
Answer: A
Explanation:
https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Mobility/WiFiLBSDG/wifich2.html
QUESTION 97
The CTO of an organization wants to ensure that all Android devices are placed into a separate VLAN on their wireless network. However, the CTO does not want to deploy ISE.
Which feature must be implemented on the Cisco WLC?
A. RADIUS server overwrite interface
B. AAA override
C. WLAN local policy
D. custom AVC profile
Answer: C
Explanation:
https://www.cisco.com/c/en/us/td/docs/wireless/controller/technotes/7- 5/NativeProfiling75.html
QUESTION 98
What must be configured on the Global Configuration page of the WLC for an AP to use 802.1x to authenticate to the wired infrastructure?
A. supplicant credentials
B. RADIUS shared secret
C. local access point credentials
D. TACACS server IP address.
Answer: A
Explanation:
Choose Wireless > Access Points > Global Configuration to open the Global Configuration page. Under 802.1x Supplicant Credentials, select the 802.1x Authentication check box. In the Username text box, enter the username that is to be inherited by all access points that join the controller.
https://www.cisco.com/c/en/us/td/docs/wireless/controller/7-6/configuration-guide/b_cg76/b_cg76_chapter_01101000.pdf
QUESTION 99
Refer to the exhibit. An engineer needs to manage non-802.11 interference.
What is observed in the output on PI?
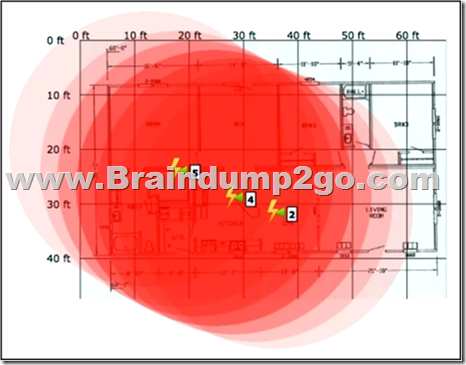
A. Several light interferers are collectively impacting connectivity at this site.
B. The three Individual clusters shown Indicate poor AP placement.
C. At least one strong interferer is impacting connectivity at this site.
D. RF at this site is unable provide adequate wireless performance.
Answer: A
Explanation:
Show Zone of Impact—Displays the approximate interference impact area. The opacity of the circle denotes its severity. A solid red circle represents a very strong interferer that likely disrupts Wi-Fi communications, a light pink circle represents a weak interferer.
We can see an area where the circles overlap and create what is close to a solid red circle, however the fact that each lightning bolt has a number greater than 1 this makes B the best choice as they seem to want to put emphasis on the number of interferers rather than the severity.
https://www.cisco.com/c/en/us/td/docs/net_mgmt/prime/infrastructure/3-7/user/guide/bk_CiscoPrimeInfrastructure_3_7_0_User_Guide/bk_CiscoPrimeInfrastructure_3_7_0_User_Guide_chapter_01001.html
QUESTION 100
A customer is deploying local web authentication. Which software application must be implemented on Cisco ISE to utilize as a directory service?
A. Solaris Directory Service
B. LDAP
C. SAML
D. Novell eDirectory
Answer: B
QUESTION 101
What must be configured on ISE version 2.1 BYOD when using Single SSID?
A. no authentication
B. WPA2
C. open authentication
D. 802.1x
Answer: D
Explanation:
https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/216535-configure-single-ssid-wireless-byod-on-w.html
QUESTION 102
The security learn is concerned about the access to all network devices, including the Cisco WLC. To permit only the admin subnet to have access to management, a CPU ACL is created and applied. However, guest users cannot get to the web portal.
What must be configured to permit only admins to have access?
A. The guest portal must be configured on the CPU ACLs on the Cisco WLC.
B. Access to Cisco ISE must be allowed on the pre authentication ACL.
C. Management traffic from the guest network must be configured on the ACL rules.
D. Traffic toward the virtual interface must be permitted.
Answer: B
Explanation:
QUESTION 103
A network engineer has been hired to perform a new MSE implementation on an existing network. The MSE must be installed in a different network than the Cisco WLC. Which configuration allows the devices to communicate over NMSP?
A. Allow UDP/16113 port on the central switch.
B. Allow TCP/16666 port on the router.
C. Allow TCP/16113 port on the firewall.
D. Allow UDP/16666 port on the VPN router.
Answer: C
Explanation:
https://www.cisco.com/en/US/docs/wireless/mse/3350/6.0/CAS/configuration/guide/msecg_ch4_CAS.html

QUESTION 104
A company has a single WLAN configured for 802.1x authentication with the QoS set to Silver. This WLAN supports all corporate and BYOD access. A decision has been made to allow users to install Cisco Jabber on their personal mobile devices. Users report poor voice quality when using Jabber. QoS is being applied only as best effort. What must be configured to ensure that the WLAN remains on the Silver class and to ensure Platinum class for Jabber?
A. Configure an AVC profile for the Jabber traffic and apply it to the WLAN.
B. Configure the WLAN to broadcast on 5 GHz radios only and allow Jabber users to conned.
C. Enable Cisco Centralized Key Management on the WLAN so that the Jabber-enabled devices will connect.
D. Configure QoS on the mobile devices that have Jabber installed.
Answer: A
Explanation:
https://www.cisco.com/c/en/us/td/docs/wireless/controller/technotes/81/Jabber_in_WLAN/b_Jabber_in_WLAN.html#reference_7B4539C91FBE4639ACF906F6F3931667

QUESTION 105
The security policy mandates that only controller web management traffic is allowed from the IT subnet. In testing, an engineer is trying to connect to a WLAN with Web Authentication for guest users, but the page is timing out on the wireless client browser.
What is the cause of this issue?
A. Web Authentication Redirect is supported only with Internet Explorer, and the client is using Google Chrome.
B. The DNS server that is configured on the controller is incorrect
C. Web Authentication Redirect is not supported with CPUACLS.
D. The implemented CPU ACL on the controller is blocking HTTP/HTTPS traffic from the guest clients.
Answer: D
QUESTION 106
All APs are receiving multicast traffic, instead of only the APs that need it. What is the cause of this problem?
A. The multicast group includes all APs
B. The wrong multicast address was used
C. The multicast group is assigned the wrong VLAN
D. Multicast IGMP snooping is not enabled
Answer: D
Explanation:
https://www.cisco.com/c/en/us/td/docs/wireless/controller/74/configuration/guides/consolidated/b_cg74_CONSOLIDATED/b_cg74_CONSOLIDATED_chapter_01011.html
QUESTION 107
Refer to the exhibit. A customer has implemented Cisco FlexConnect deployments with different WLANs around the global and is opening a new branch in a different location. The engineers’ task is to execute all the wireless configuration and to suggest how to configure the switch ports for new Aps. Which configuration must the switching team use on the switch ports?
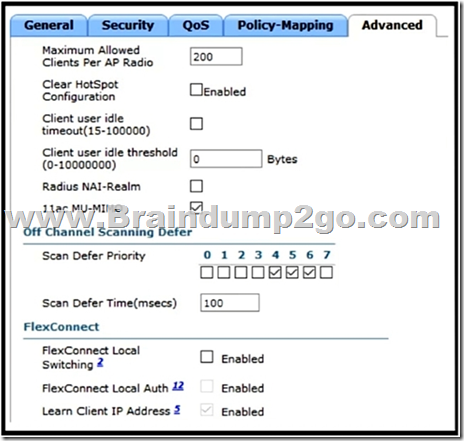
A. Multiple VLAN
B. Access mode
C. Trunk mode
D. Single mode
Answer: C
QUESTION 108
After looking in the logs, an engineer notices that RRM keeps changing the channels for non-IEEE 802. 11 interferers. After surveying the area, it has been decided that RRM should not change the channel. Which feature must be enabled to ignore non-802.11 interference?
A. Avoid Cisco AP Load
B. Avoid Persistent Non-WIFI Interference
C. Avoid Foreign AP Interference
D. Avoid Non-802.11 Noise
Answer: B
Explanation:
Check the Avoid Non-802.11a (802.11b) Noise check box to cause the controller’s RRM algorithms to consider noise (non-802.11 traffic) in the channel when assigning channels to lightweight access points, or uncheck it to disable this feature. For example, RRM may have access points avoid channels with significant interference from nonaccess point sources, such as microwave ovens. The default value is selected.
Check the Avoid Persistent Non-WiFi Interference check box to configure the controller to stop ignoring persistent non-Wi-Fi interference in new channel calculation. The persistent non-Wi-Fi interference is considered during the metric calculation for channels.
https://www.cisco.com/c/en/us/td/docs/wireless/controller/8-6/config-guide/b_cg86/radio_resource_management.html
QUESTION 109
An engineer is configuring multicast for two WLCs. The controllers are in deferent physical locations and each handles around 500 wire clients. How should the CAPWAP multicast group address be assigned during configuration?
A. Each WLC must be assigned a unique multicast group address
B. Each WLC management address must be in the same multicast group
C. Each WLC management address must be in a different multicast grou
D. Both WLCs must be assigned the same multicast group address
Answer: A
Explanation:
Choose Controller > General to configure AP multicast mode (multicast or unicast) & CAPWAP multicast group address(only for multicast mode). Use private multicast IP (239.0.0.0/8) for the group address, but avoid 239.0.0.x or 239.128.0.x as these overlap with the link local MAC addresses & flood out all switch ports. This group address cannot be used for any application in your network. If you have multiple controllers, configure different group address for different controllers.
https://mrncciew.com/2012/11/17/configuring-multicast-on-wlc/
QUESTION 110
An engineer must implement a BYDD policy with these requirements:
– Onboarding unknown machines
– Easily scalable
– Low overhead on the wireless network
Which method satisfies these requirements?
A. triple SSID
B. open SSID
C. dual SSID
D. single SSID
Answer: D
Explanation:
https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Borderless_Networks/Unified_Access/BYOD_Design_Guide/BYOD_Wireless.html
Resources From:
1.2023 Latest Braindump2go 300-430 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/300-430.html
2.2023 Latest Braindump2go 300-430 PDF and 300-430 VCE Dumps Free Share:
https://drive.google.com/drive/folders/16vzyRXoZZyqi0Y–JVJl_2HlEWTVkB2N?usp=sharing
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!
[March-2023]Full Version 300-835 Dumps PDF and VCE 300-835 70Q for Free Download[Q12-Q52] [March-2023]Braindump2go AZ-500 Dumps VCE Dumps Free Download[Q239-Q278]
Comments are currently closed.