23 12 2015
[OFFICIAL]Braindump2go 70-646 Study Guide Download (161-170)
MICROSOFT NEWS: 70-646 Exam Questions has been Updated Today! Get Latest 70-646 VCE and 70-646 PDF Instantly! Welcome to Download the Newest Braindump2go 70-646 VCE&70-646 PDF Dumps: http://www.braindump2go.com/70-646.html (283 Q&As)
The 70-646 Exam Practice Questions and Answers are ideal for the aspring candiates to grab exceptional grades in Microsoft 70-646 Exam! The 70-646 Questions and Answers are developed using the latest updated course content and all the answers are verified to ensure phenoment preparation for the actual 70-646 Exam!
Exam Code: 70-646
Exam Name Windows Server 2008, Server Administrator
Certification Provider: Microsoft
Corresponding Certifications: MCSA, MCSA: Windows Server 2008, MCSE, MCSE: Private Cloud Windows Server 2008
70-646 Dumps,70-646 Study Guide,70-646 Exam Questions,70-646 eBook,70-646 eBook PDF,70-646 Dumps PDF,70-646 Dumps Latest,70-646 Book,70-646 Braindumps,70-646 Braindump PDF,70-646 Braindump Free,70-646 Practice Test,70-646 Practice Questions,70-646 PDF eBook,70-646 PDF,70-646 VCE

Case Study 8 – Fabrikam Inc (QUESTION 161 – QUESTION 167)
COMPANY OVERVIEW
Fabrikam Inc. is a manufacturing company that has a main office and a branch office.
PLANNED CHANGES
You plan to deploy a failover cluster named Cluster1 in the branch office.
Cluster1 will be configured to meet the following requirements:
– The cluster will host eight virtual machines (VMs).
– The cluster will consist of two nodes named Node1 and Node2.
– The quorum mode for the cluster will be set to Node and Disk Majority.
– A user named Admin1 will configure the virtual switch configuration of the VMs.
– The cluster nodes will use shared storage on an iSCSI Storage Area Network (SAN).
You plan to configure a VM named File2 as a file server.
Users will store confidential files on File2.
You plan to deploy a Microsoft Forefront Threat Management Gateway (TMG) server in each site.
The Forefront TMG server will be configured as a Web proxy.
EXISTING ENVIRONMENT
The research department is located in the branch office.
Research users frequently travel to the main office.
Existing Active Directory/Directory Services
The network contains a single-domain Active Directory forest named fabrikam.com.
The functional level of the forest is Windows Server 2008.
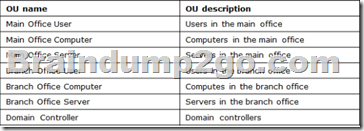
The relevant organizational units (OUs) for the domain are configured as shown in the following table.
The relevant sites for the network are configured shown in the following table.
The relevant group policy objects (GPOs) are configured as shown in the following table.
Existing Network Infrastructure
All users run windows server 2008 R2.
The relevant servers are configured as shown in following table.
WSUS2 is configured as a downstream replica server.
File1 contains a share named Templates.
Users access the Templates share by using the path \\fabrikam.com\dfs\templates.
File1 has the Distributed File System (DFS) Replication role service and the DFS Namespaces role service installed.
TECHNICAL REQUIREMENTS
Fabrikam must meet the following requirements:
– Minimize the cost of IT purchases.
– Minimize the potential attack surface on the servers.
– Minimize the number of rights assigned to administrators.
– Minimize the number of updates that must be installed on the servers.
– Ensure that Internet Explorer uses the local ForeFront TMG server to connect to the Internet.
– Ensure that all client computers continue to receive updates from WSUS if a WSUS server fails.
– Prevent unauthorized users from accessing the data stored on the VMs by making offline copies of the VM files.
Fabrikam must meet the following requirements for the Templates share:
– Ensure that users access the files in the Templates share from a server in their local site.
– Ensure that users always use the same UNC path to access the Templates share, regardless of the site in which the users are located.
QUESTION 161
You need to configure Internet Explorer to meet the company’s technical requirements.
Which GPO or GPOs should you modify?
A. Default Domain Policy
B. GPO1
C. GPO2 and GPO3
D. GPO4 and GPO5
Answer: D
Explanation:
The company has 2 sites
He following list contains example applications of policy:
A GPO linked to a site applies to all users and computers in the site.
A GPO applied to a domain applies to all users and computers in the domain and, by inheritance, to all users and computers in child organizational units. Be aware that policy is not inherited across domains.
A GPO applied to an organizational unit applies directly to all users and computers in the organizational unit and, by inheritance, to all users and computers in child organizational units.
QUESTION 162
You need to recommend the minimum number of logical unit numbers (LUNs) that must be provisioned for Cluster1.
The recommendation must support the company’s planned changes.
Which number should you recommend?
A. 1
B. 2
C. 8
D. 9
Answer: B
QUESTION 163
You need to recommend a strategy for delegating administrative rights to Admin1.
The strategy must support the company’s planned changes.
What should you include in the recommendation?
A. the Authorization Manager snapin on Node1 and Node2
B. the Authorization Manager snapin on the VMs
C. the Network Configuration Operators local group on each VM
D. the Network Configuration Operators local group on Node1 and Node2
Answer: A
Explanation:
http://technet.microsoft.com/en-us/library/cc731364.aspx
An authorization store can contain authorization policy information for many applications in a single policy store. All applications in one authorization store can access all of the groups defined at the store level.
You must be assigned to the Authorization Manager Administrator user role to complete this procedure. By default, Administrators is the minimum Windows group membership assigned to this role. Review the details in “Additional considerations” in this topic
QUESTION 164
You need to configure Windows Update to meet the company’s technical requirements.
What should you do?
A. Configure WSUS2 as an autonomous server.
B. Create a Network Load Balancing (NLB) cluster.
C. Create multiple Host (A) records and use round robin DNS.
D. Configure multiple service location (SRV) records and use round robin DNS.
Answer: B
Explanation:
http://technet.microsoft.com/en-us/library/dd939896%28WS.10%29.aspx
Network load balancing (NLB) is an optional feature of Windows Server that load balances network traffic for high availability. You can install Windows Server Update Services (WSUS) 3.0 SP2 in a network that uses NLB, but this configuration requires that you perform additional steps during WSUS setup.
QUESTION 165
You need to protect the confidential data files on File2 against unauthorized offline access.
What should you use?
A. Encrypting File System (EFS) on File2
B. file screens on Node1 and Node2
C. NTFS permissions on File2
D. Windows BitLocker Drive Encryption (BitLocker) on Node1 and Node2
Answer: A
Explanation:
http://technet.microsoft.com/en-us/library/cc749610%28WS.10%29.aspx
Per-user encryption of offline files Offline copies of files from remote servers can also be encrypted by using EFS. When this option is enabled, each file in the offline cache is encrypted with a public key from the user who cached the file. Thus, only that user has access to the file, and even local administrators cannot read the file without having access to the user’s private keys.
QUESTION 166
You need to recommend a file access solution for the Templates share.
Which two actions should you recommend? (Each correct answer presents part of the solution. Choose two.)
A. Add File2 as a namespace server for \\fabrikam.com\dfs.
B. Add \\File2\templates as a folder target for \\fabrikam.com\dfs\templates.
C. In the Group Policy preferences of GPO2 and GPO3, add new mapped drives.
D. Create a DFS Replication group that contains \\File1\templates and \\File2\templates.
Answer: BD
QUESTION 167
You need to recommend an operating system for Node1 and Node2.
The recommendation must meet the company’s technical requirements.
Which operating system image should you install?
A. a full installation of Windows Server 2008 R2 Enterprise
B. a full installation of Windows Server 2008 R2 Standard
C. a Server Core installation of Windows Server 2008 R2 Enterprise
D. a Server Core installation of Windows Server 2008 R2 Standard
Answer: C
Explanation:
By using server core you minimize the surface attack area
Case Study 9 – Litware, Inc (QUESTION 168 – QUESTION 174)
COMPANY OVERVIEW
Litware, Inc. is a manufacturing company that has a main office and two branch office.
The main office is located in Montreal.
The branch offices are located in Seattle and New York.
The main office has 4,000 users.
The branch offices each have 500 users.
PLANNED CHANGES
Litware plans to open a new sales office.
The sales office will have a direct connection to the Internet.
The sales office will have a single server.
The sales office requires a connection to the Montreal office.
The connection to the Montreal office must use either TCP port 80 or TCP port 443.
The network currently contains a Fibre Channel Storage Area Network (SAN).
A new iSCSI SAN will be implemented during the next month.
The current SAN and the new SAN are from different manufacturers.
Both SANs use a virtual disk service (VDS) interface.
EXISTING ENVIRONMENT
All servers run Windows Server 2008 R2.
All client computers run Windows 7 Enterprise.
The main office has a single DHCP server.
The IP addresses for all of the client computers must be assigned from the DHCP server.
All software is installed from a central software distribution point in the main office.
Software deployments for the branch offices frequently fail due to bandwidth limitations.
Existing Active Directory/Directory Services
The network contains a single Active Directory domain named litwareinc.com. Each office has two domain controllers.
Current Administration Model
Currently, all help desk users have full administrator rights to the servers.
The help desk users use Remote Desktop to log on to the servers and perform tasks such as managing Active Directory user accounts and creating DHCP reservations.
TECHNICAL REQUIREMENTS
Windows Firewall must be managed by using the minimum amount of administrative effort.
Windows Firewall configurations must be duplicated easily between servers that have the same server role.
Litware must centralize the monitoring of critical system events.
The monitoring solution must use the existing infrastructure.
Litware plans to prevent help desk users from interactively logging on to servers.
Help desk users must not have full administrator rights to the servers.
The software deployment process must be updated to meet the following requirements:
– Application source files must be centrally managed.
– Software deployments to the offices in Seattle and New York must remain unaffected if a WAN link fails.
The SANs must be administered by using a single tool.
QUESTION 168
You need to recommend changes to the software deployment process that meet the company’s technical requirements.
What should you include in the recommendation?
A. BranchCache in Distributed Cache mode
B. BranchCache in Hosted Cache mode
C. domain-based Distributed File System (DFS)
D. standalone Distributed File System (DFS)
Answer: C
QUESTION 169
You need to recommend a tool to manage the SANs.
The tool must support the company’s planned changes and technical requirements.
Which tool should you recommend?
A. Disk Management
B. Share and Storage Management
C. Storage Explorer
D. Storage Manager for SANs
Answer: D
Explanation:
http://technet.microsoft.com/en-us/library/cc754551%28WS.10%29.aspx
Storage Manager for SANs is a Microsoft Management Console (MMC) snap-in that helps you create and manage logical unit numbers (LUNs) on Fibre Channel and Internet SCSI (iSCSI) disk drive subsystems that support Virtual Disk Service (VDS) in your storage area network (SAN).
QUESTION 170
You need to recommend a VPN solution for the new sales office.
The solution must support the company’s planned changes.
What should you include in the recommendation?
A. Internet Key Exchange version 2 (IKEv2)
B. Layer 2 Tunneling Protocol (L2TP)
C. PointtoPoint Tunneling Protocol (PPTP)
D. Secure Socket Tunneling Protocol (SSTP)
Answer: D
Explanation:
http://support.microsoft.com/kb/947032
SSTP is a new kind of Virtual Private Networking (VPN) tunnel that is available in the Routing and
Remote Access Server role in Windows Server 2008. SSTP allows for Point-to-Point Protocol
(PPP) packets to be encapsulated over HTTP. This allows for a VPN connection to be more easily established through a firewall or through a Network Address Translation (NAT) device. Also, this allows for a VPN connection to be established through an HTTP proxy device.
The information is this article is more likely to apply to a small-sized or medium-sized organization.
For these kinds of organizations, it is common to have one public IP address that is assigned to the external interface of a NAT router or of a gateway device.
This article describes the following scenario:
You have a Windows Server 2008-based Secure Socket Tunneling Protocol (SSTP)-based VPN server.
The server is assigned a private IP address.
The server is located on an internal network behind a NAT device.
Braindump2go New Updated 70-646 Exam Dumps are Complete Microsoft 70-646 Course Coverage! 100% Real Questions and Correct Answers Guaranteed! Updated 70-646 Preparation Material with Questions and Answers PDF Instant Download:
FREE DOWNLOAD: NEW UPDATED 70-646 PDF Dumps & 70-646 VCE Dumps from Braindump2go: http://www.braindump2go.com/70-646.html (283 Q&As)
2015 70-646 Exam Questions PDF Free Download From Braindump2go (141-150) [FREE]Braindump2go 70-646 Exam PDF Download (171-180)
![image_thumb[1] image_thumb[1]](http://examgod.com/bdimages/59c39c8c2bb3_C1ED/image_thumb1_thumb.png)
![image_thumb[2] image_thumb[2]](http://examgod.com/bdimages/59c39c8c2bb3_C1ED/image_thumb2_thumb.png)
![image_thumb[3] image_thumb[3]](http://examgod.com/bdimages/59c39c8c2bb3_C1ED/image_thumb3_thumb.png)
Comments are currently closed.